Hi there,
I’ve been banging my head about this topic for quite some time now but can’t figure it out, so any help I can get would be much appreciated ![]()
Current status:
I’ve Axigen v10.6.1 Free running on my server. To serve the WebMail and WebAdmin I have set two domains, wanda.cubyx.pro and axel.cubyx.pro respectively. Traefik is routing request to these services over SSL with no trouble.
I was also able to setup mail.cubyx.pro at the DNS and Traefik level to be able to generate an SSL certificate with Let’s Encrypt from the WebAdmin, bypassing Traefik for this one.
Where trouble begins:
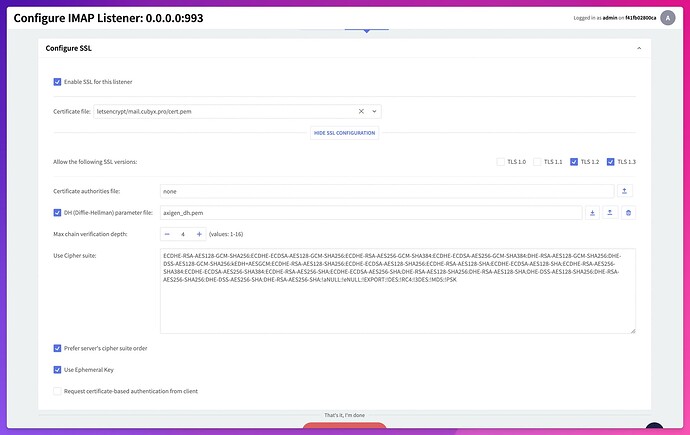
Once the certificate was generated, I was able to select it in the SSL config of the IMAP and SMTP listeners.
Sadly when I try to open a secure IMAP or SMTP connection to mail.cubyx.pro, the certificate cannot be fully verified and thus the connection fails.
$ openssl s_client -connect mail.cubyx.pro:993 -showcerts
Connecting to 38.102.125.117
CONNECTED(00000005)
depth=0 CN=mail.cubyx.pro
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN=mail.cubyx.pro
verify error:num=21:unable to verify the first certificate
verify return:1
depth=0 CN=mail.cubyx.pro
verify return:1
---
Certificate chain
0 s:CN=mail.cubyx.pro
i:C=US, O=Let's Encrypt, CN=R11
a:PKEY: rsaEncryption, 4096 (bit); sigalg: RSA-SHA256
v:NotBefore: Dec 26 13:22:54 2024 GMT; NotAfter: Mar 26 13:22:53 2025 GMT
-----BEGIN CERTIFICATE-----
... certificate content here ...
-----END CERTIFICATE-----
---
Server certificate
subject=CN=mail.cubyx.pro
issuer=C=US, O=Let's Encrypt, CN=R11
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2334 bytes and written 405 bytes
Verification error: unable to verify the first certificate
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Protocol: TLSv1.3
Server public key is 4096 bit
This TLS version forbids renegotiation.
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 21 (unable to verify the first certificate)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 0DE55CA6E7939A2F4E241EA3612F285817F2FB5D31ADEB5759D6A3C49A0E1D7A
Session-ID-ctx:
Resumption PSK: 6D0311145754000864ABD7E7F6AA7972D1CAB3171C428482C7D250724A132BB0565170F725AED1884A35C6AAF2FFF737
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
[...snip...]
Start Time: 1735507179
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 18A47CA380EBD43A864A188C36F8F41B660EB3F5567F818F51C5EEEA53EEB74F
Session-ID-ctx:
Resumption PSK: 941FAB7E95C526A4C87ED06EFB3E5608B5168B57AA327936531A5540816C747585F96DEB7EEDF2935F82F081F818FD43
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
[...snip...]
Start Time: 1735507179
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
* OK AXIGEN IMAP4rev1 service is ready
What I’ve tried:
Looking in various places and forums, and discussing with ChatGPT, I tried a few things like merging cert.pem and cert_auth.pem into fullchain.pem, with and without the key, importing it manually from the WebAdmin, or overriding cert.pem with it, but no dice.
Once again, I’d be grateful for any guidance ![]()
Thanks! ![]()