Too many domains will work under the MSP license. In this case, should DKIM be created for each domain? In other words, doesn’t the default domain’s DKIM cover all domains?
Hello,
Usually each hosted domain should have its own signing rule.
However you may have a single signing rule and adapt it to use the same selector and private key for all domains.
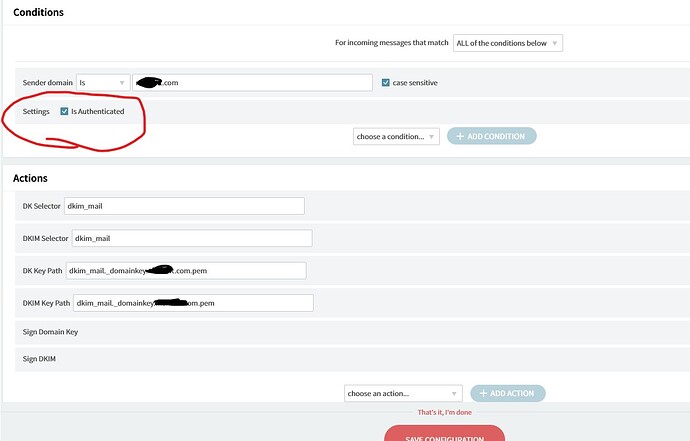
This is easy to do by keeping only the following condition:
Connection is authenticated (ticked)
HTH,
Ioan
remove sender domain condition and test again.
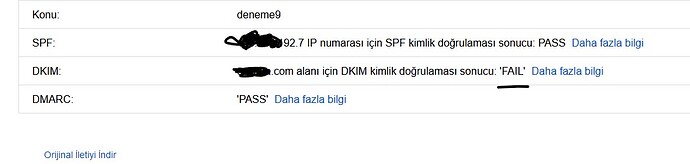
Yes… Now, I removed sender domain… and result : fail for 2th domain…
but, default domain result : pass
did you put the public key into the DNS of all hosted domains?
No, İ did not. I could not… How can I put all hosted domains? Can you give a example?
well - in this situation (you / end-user can not put the public key into the DNS) than the DKIM signed messages could not be verified.
as you know, signing and verifying the message are 2 separate processes:
1/ for signing: the private key is used to sign the message
2/ for verification: the public key is needed for verification purposes
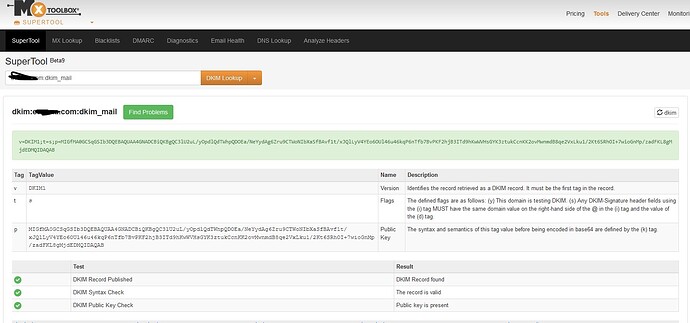
the public key is retrievable from DNS (via a TXT record) knowing that its name is based on the so called “selector”.
bottom line - if the public key could not be added into DNS than signing the message is useless.
HTH,
Ioan
Dkim is true on mxtoolbox.com… But, Fail on Gmail…
I think, I must do something on server… TXT DNS record is correct. but gmail cannot verify. What should I do?
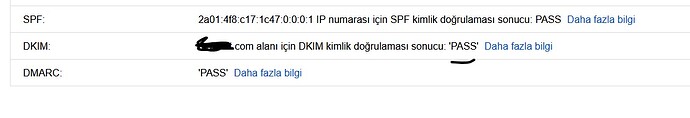
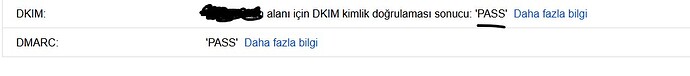
Now DKIM is approved by gmail.
I was making the mistake.
I want to write my mistake here. So that others do not make the same mistake.
I thought that a separate DKIM would be created for each hosted domain. No. You should use the DKIM you created for your default domain for the hosted domains. And you should enter DNS TXT for each domain you host. You can find the necessary steps for Gmail approval on this page of Axigen. The necessary file should be on your server as in this link: DNS Configuration | Axigen Documentation
Thanks @indreias