1. Authentication / Encryption
The Axigen server supports authentication, meaning it can be instructed to accept only connections / messages from authenticated entities. To reduce the risk of unauthorized access and suspicious connections, Axigen has the following methods — in this specific order — available for client authentication:
- CRAM-MD5
- LOGIN
- PLAIN
- DIGEST-MD5
- GSSAPI
SSL / TLS
All Axigen communication protocols can benefit from SSL / TLS technology which allows you to send encrypted emails across networks, preventing plain text messages to be intercepted on the way from sender to recipient. This encryption method guarantees secure data transmission over networks.
2. Multi-layer Access Control
Stopping spammers and preventing DOS attacks is one of the most important tasks to ensure a mail server is secure and the sooner the problem is identified in the mail stream, the better. This is why Axigen has built-in access control at the application (TCP listener) level that allows the administrator(s) to control connectivity parameters.
Furthermore, administrators may define IP sets that have specific sets of such rules, applied with different priorities, or IP sets from which connections are denied.
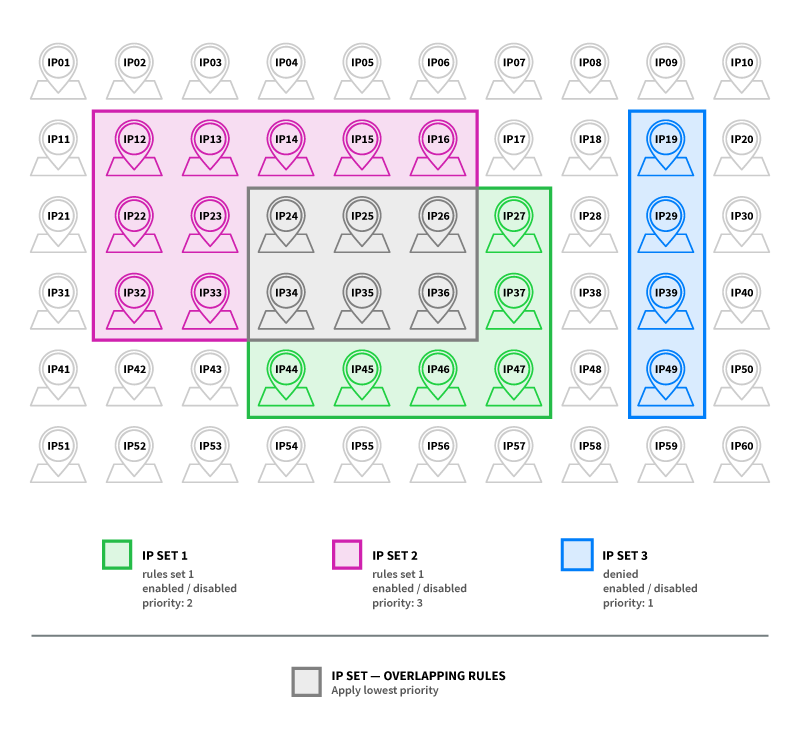
3. Flow Control
Flow control restrictions can be defined in addition to the access control rules, in order to prevent server and storage overload, as well as to protect the server from DDoS attacks.
Restrict Maximum Simultaneous Connections
Restrict the total number of simultaneous connections that a service may accept, the maximum number of simultaneous connections accepted from the same IP address in order to avoid attacks from a single IP. Additionally, privileged IP address groups (trusted servers) may have different connection limits policies.
Restrict Maximum Incoming Connections Rate
Restrict the total number of connections per time unit that a service may accept, the maximum number of connections per time unit accepted from the same IP address in order to avoid attacks from a single IP. Additionally, privileged IP address groups (trusted servers) may have different connection rate limits policies.
Selectively Restrict Maximum Message Size
The server can be configured to accept different maximum message sizes based on:
- sender / sender domain
- recipient / recipient domain
- remote IP address, connection security
- authentication level
- and other message or connection related parameters
This process ensures flexible protection of the queue and the storage (privileged users may have extended rights).
4. SPF (Sender Policy Framework)
Axigen uses a standard-based Sender Policy Framework (SPF) verification module for sender validation (if the remote domain is properly configured with SPF information).
SPF protects email users from unwanted messages, but one big downside is that attempting to send emails from a hosted domain to a Gmail address, for example, may not work reliably. That’s why, starting with Axigen X3 Update 2, we introduced SRS:
Sender Rewriting Scheme (SRS)
SRS is a scheme for rewriting an email’s envelope sender in order to remail it. The scheme allows you to use your own domain where you have control over the relevant SPF records, basically rewriting your Sender address so that it appears to come from the forwarding mail server. This functionality works well for sending official work emails to personal email addresses.
You can read more about how sender rewriting scheme works here.
5. DKIM (DomainKeys Identified Mail)
The integrity of messages in Axigen may be checked if the originating server used DKIM to sign them; locally-originated messages are signed by Axigen to allow validation by DKIM-compliant remote servers (many receiving servers associate a higher spam score to unsigned messages).
At Axigen we also implemented DKIM to protect users’ inboxes from unwanted messages and mitigate spam, spoofing, phishing scams, forgery, and email based viruses. It works by essentially adding a digital signature to email headers which is then validated against a public cryptographic key in the Sender’s DNS. You can learn more about how DKIM functions here and get instructions on how to implement an advanced DKIM configuration in Axigen here.
6. DMARC (Domain-based Message Authentication, Reporting & Conformance)
On top of SPF and DKIM, there is DMARC. This email authentication policy and reporting protocol works on top of the previous systems by adding the following:
- A link to the author domain name in the email header
- Published policies for recipient handling of authentication failures
- Reporting from receivers to senders
DMARC helps monitor and improve domain protection from harmful emails. It works by adding a layer of security beyond SPF and DKIM. If both fail, then the DMARC protocol will also fail. Overall, implementing DMARC makes your domain more secure, guarding it against business email compromise attacks, phishing, scams, and other cybersecurity concerns.
See how you can configure DMARC in Axigen and how you can integrate Axigen with openDMARC through Milter V6.
7. Blacklisting / Whitelisting
The blacklist feature allows you to permanently reject emails coming from untrusted senders. This can be defined globally by the administrator (server level) and further refined by the users according to their personal needs (WebMail interface). More information on using blacklists in Axigen.
Administrators can also define Whitelists in order to permanently accept emails coming from trusted sources (such as business partners or remote offices). More information on setting up a whitelist in Axigen.
8. Greylisting
This feature enables Axigen to automatically reject messages from unknown senders / IPs with a temporary error message. Unlike legitimate email servers, most spam sources will not try to resend the spam or malicious emails in question, thus reducing the number of unwanted emails received by the Axigen server.
Read more: What greylisted means and how it affects your emails.
9. Country Filtering
Based on an IP-to-country database, administrators can block all emails coming from untrusted countries; alternatively they can accept emails coming exclusively from selected countries.
10. DNSBL
Administrators validate sender IPs against a selected list of DNSBLs (DNS Blacklists) in order to block emails; at the same time, they can also choose to skip this validation for custom defined IP Ranges. For increased protection, you can add Axigen's premium DNSBL & URIBL blacklist services.
11. URIBL
Administrators also validate the URIs contained in the incoming emails against a domain-based blocklist that checks if the URIs are labeled as phishing sources. If they are, then the email is rejected, labeled, or delivered based on the admin setup in place.
Axigen’s URI BlockList (aURIBL) aggregates data from several commercial lists of phishing sources, as well as from Axigen threat intelligence research. Learn more about the advantages of our aDNSBL and aURIBL here.
To install and configure aDNSBL and aURIBL your Axigen server, check the following guides:
Once installed, you can also obtain logs from your aDNSBL and aURIBL setups to check relevant stats.
12. DNS Checks
Additional validations that can be run to reject spam are by checking the originating domain for MX entries and the originating IP for a reverse DNS entry.
13. AntiVirus Filtering
The advanced Axigen content filtering system allows the system administrator to define a set of filters and priorities either at server level (gateway SMTP server or the SMTP Receiving / SMTP Sending service), or at domain / user level (Processing), thus offering unparalleled flexibility to set up security policies:
- Domain 1: filter with 2 AV and 1 ASPAM applications
- Domain 2: filter with only 1 AV
- General Manager: filter with 3 AV and 1 ASPAM applications
Embedded AntiMalware Protection
Axigen offers premium, scalable defense against Malware threats by leveraging the advanced malware detection engine powered by Bitdefender.
Multiple AntiVirus & AntiSpam Filtering via Milter
Axigen additionally offers Milter support, thus extending the security applications pool by integrating with virtually any Milter capable AntiVirus or AntiSpam application.
14. AntiSpam Filtering
After applying the above mentioned antispam methods, the remaining traffic is further taken through a content filtering process (score based). Administrators can set the thresholds over which the corresponding reject actions will be applied.
Intelligent AntiSpam Technology
Bitdefender had an average spam detection rate of over 99.9% with zero false positives in the latest 22 consecutive VBSpam tests, and has achieved Virus Bulletinʼs highest certification, VBSpam+, for 22 tests in a row as of March 2020.
15. Filtered Email and Identity Confirmation
Filtered email allows end-users to apply a special treatment (discard, send NDR, store them in a special "Filtered Email" folder, and / or apply Identity Confirmation) for emails from new / untrusted senders.
Axigen Identity Confirmation© a Challenge / Response antispam method. It enables users to effectively block unwanted messages from reaching their inbox by intercepting incoming emails and requiring new / unknown senders to confirm their identity, while allowing legitimate communications to come through.
16. Message Acceptance / Sending Policies
The Axigen server includes an advanced Message Acceptance / Sending policies engine. Here are some examples:
-
Reject:
- emails from impersonated users (authentication matching)
- emails from unauthenticated users
- emails suspicious to be spam (e.g. looping emails, emails with too large attachments and others)
- Require validation for emails coming from unknown sources
-
Accept:
- emails coming from trusted sources (Whitelisting)
- secure connections only
17. Routing Policies
Virtual routing
Axigen allows you to assign different outbound IP addresses to each domain. Blacklisted IPs will only affect the associated domain, and not other domains operating on the same server.
Example:
- relay emails from domain 1 to route 1, using IP1
- relay emails from all other domains to route 2, using IP2
- specify a username / password authentication before routing emails
Built in DNS Cache
DNS query responses are cached; subsequent queries are resolved locally instead of being re-sent over the network.
18. Anti-Impersonation
With Axigen’s email server security options, you can also enforce user authentication on message submission and verify that the sender header matches the authentication credentials. This prevents impersonation attempts from local accounts.
Axigen has the following message and connection parameters for its security policies*:
- Originating host's IP, ports, greeting
- Originator's email address, domain or username
- Recipient email address, routing information
- Message size, headers, number of recipients
- Connection security level (SSL / non-SSL)
- Authentication information
- Session statistics (total mails sent, total size)
- SPF interrogation result; etc
* message size, anti-impersonation, SPF, access control, email address blacklisting / whitelisting, DNS checks, open relay blocking, etc
19. Secure Passwords Enforcement
Define password strength policies (minimum password length, required sets of characters and so on), restricting the users from setting simple passwords.
20. 2-Step Verification
Axigen allows admins to enable (and even enforce) 2-Step Verification (also known as Two-Factor Authentication or simply 2FA) for WebMail users. Once enabled, users can login through compatible Time-based One-time Password (TOTP) Apps such as Google Authenticator or Microsoft Authenticator.
21. Brute-Force Attacks Protection
The Axigen mail server also offers protection from brute-force attacks through:
Fail2Ban works as an intrusion detection and prevention system that monitors log files (i.e. Axigen's security.txt) and blocks IP addresses making too many login attempts. The Axigen Admin can also set specific unwanted actions to be performed within a timeframe, thereby adding their own set of rules to protect against brute-force attacks on Linux.
RdpGuard works in a similar way by monitoring server logs and detecting failed login attempts. Admins can then set the number of failed attempts to allow before the attacker’s IP address is blocked.